Jun 2, 2025
Infrastructure of a Heist: How Credential Theft Operates at Scale
- Credential Theft is a Business with Infrastructure: Running a malware-based credential theft campaign requires an ecosystem of services—including infostealer rentals (e.g. LummaC2), bulletproof hosting, phishing kits, crypters, and SEO manipulation—costing as little as $1,363 to launch a basic operation.
- YouTube is a Growing Malware Delivery Channel: Cybercriminals increasingly exploit YouTube to distribute malware, using fake software tutorials and compromised accounts with SEO-optimized content, costing under $500 to reach massive audiences.
- Traffer Teams Professionalize Cybercrime: Credential theft is often executed by structured groups known as traffer teams. Operators’ earnings vary widely—from a few dollars to hundreds per day—depending on their investment in tools, distribution methods, and personal effort.

Jacobo Blancas
Threat Intelligence Unit

Beatriz Pimenta
Threat Intelligence Unit
Introduction
Stealing credentials at scale isn’t just about sending phishing emails or deploying malware - it requires a robust infrastructure to operate efficiently while evading detection. From domain registrations and bulletproof hosting to automated toolkits and anonymization layers, attackers build and maintain complex ecosystems to support credential theft. This post, the second part of a tripartite blog series on the credential theft ecosystem, shifts focus from victims to attackers. In our first publication, we analyzed malware-compromised credentials to understand who was affected and how. Now, we examine the infrastructure behind these campaigns, breaking down the costs and logistical requirements for cybercriminals.
Credential theft campaigns involve several key expenses, including the rental of infostealers, malware hosting services, anonymization services, and delivery mechanisms such as spam services, and phishing kits. While other operational security measures might play a role, they won’t be considered in this analysis. For this study, we focus on the primary infrastructure needed to run such campaigns and estimate the investment required for these critical components.
Infostealer rental price
The first factor considered in this analysis is the rental price of infostealers. Given that the threat actor behind the campaign lacks the technical skills or time to develop their own tool—and considering the increasing commoditization of the cybercriminal ecosystem—the easiest solution is to resort to Malware-as-a-Service (MaaS). These tools are commercially available on underground forums, marketplaces, and Telegram channels, with the first being the most accessible and transparent option for an average buyer. For this analysis, we consulted the top-tier Russian-speaking Exploit forum and looked for some of the most popular infostealers for this comparison.
LummaC2 has been one of the most prevalent stealers in operation since early 20241,2. Our own data collection at Zynap supports this finding and is consistent with our peers’ observations: we analyzed a random sample of infostealer infections by malware family from November/2024 to March/2025 and found that LummaC2 is by far the most prevalent stealer in operation, as shown in the table below:
- INSERT TABLE
To understand the costs associated with this tool, we examined its pricing structure. On Exploit, LummaC2 is offered on a tiered pricing scheme based on user privileges. All plans operate on a monthly subscription model, as detailed below:
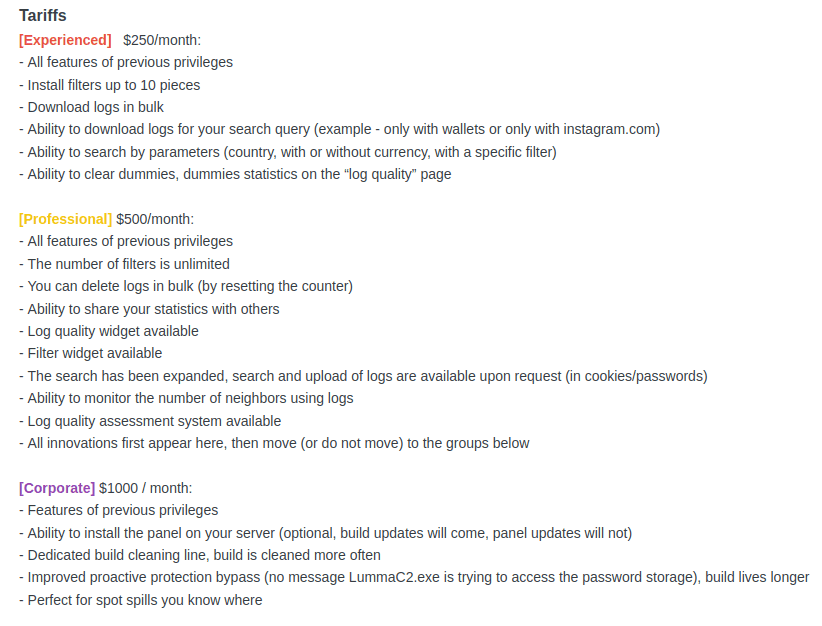
Figure 1. The forum user "Shamel" announces LummaC2 in the Exploit forum.
In addition to LummaC2, two other highly popular infostealers are commercialized on Exploit. For instance, Vidar is advertised by the user “Loadbaks” under a specific pricing structure:
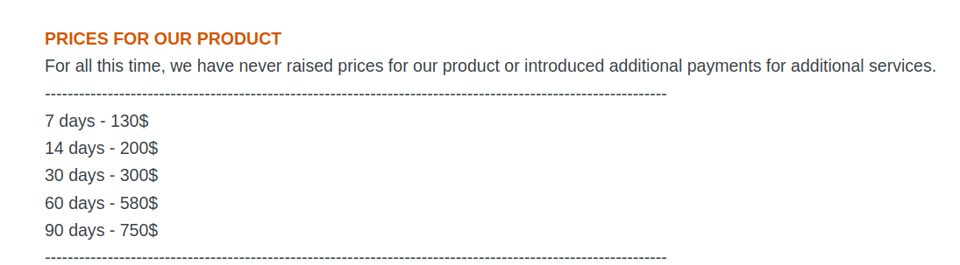
Figure 2. Vidar rental pricing scheme on Exploit.
Finally, StealC is announced by “plymouth" as follows:
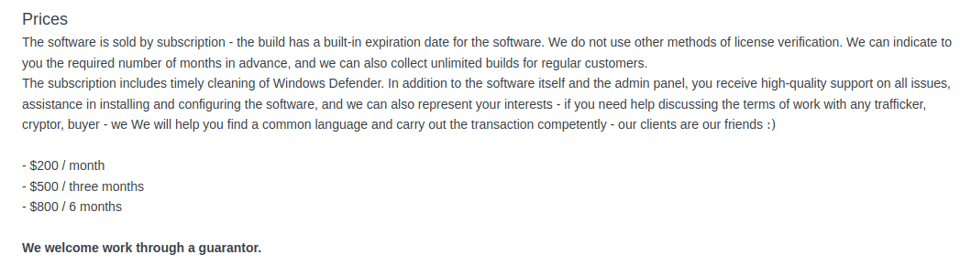
Figure 3. StealC pricing scheme on Exploit.
Comparatively, StealC is the most affordable option, priced at US$200 per month; while LummaC2 is the most expensive option with fees ranging from US$250 to US$1,000 per month. Interestingly, LummaC2 remains one of the most employed infostealers as of writing, which may be explained, if not by the price, then by its extensive capabilities, constant updates, and technical support by its operators. For comparison purposes, we consider an average rental fee of US$250 per month as the cost a threat actor must pay to launch a credential-stealing campaign.
Malware hosting services
Once the desired infostealer has been acquired, its malware panel must be hosted somewhere, and this service is another cost to be considered when launching a credential theft campaign. For this study, we consulted the also top-tier Russian-speaking XSS underground forum, looking for an average price for malware hosting services.
The selection criteria for the services below included one with a high reaction score, another with a recent posting date, and a third that appeared in pinned threads. By order of appearance above, the following pricing schemes for malware hosting services were identified:
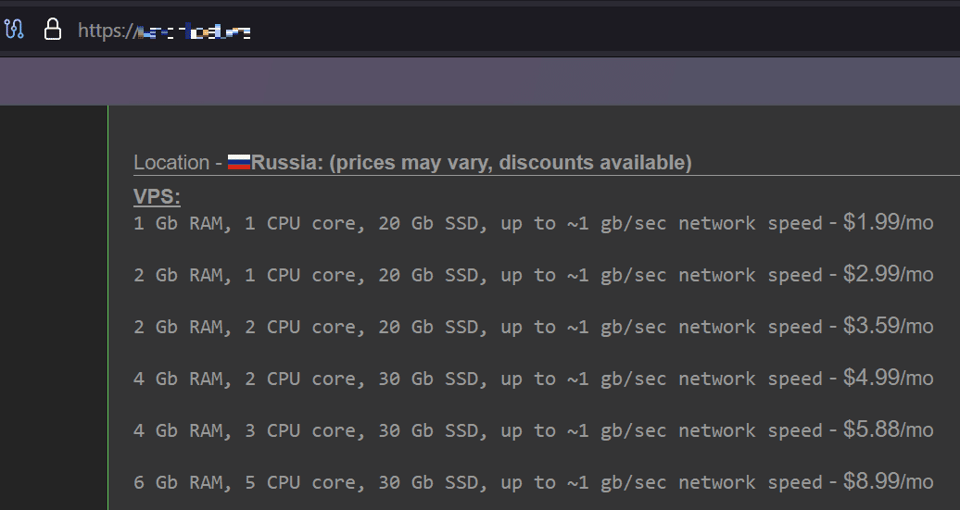
Figure 4. Webpage of one of the server services offered on XSS whose author has more reputation score points.
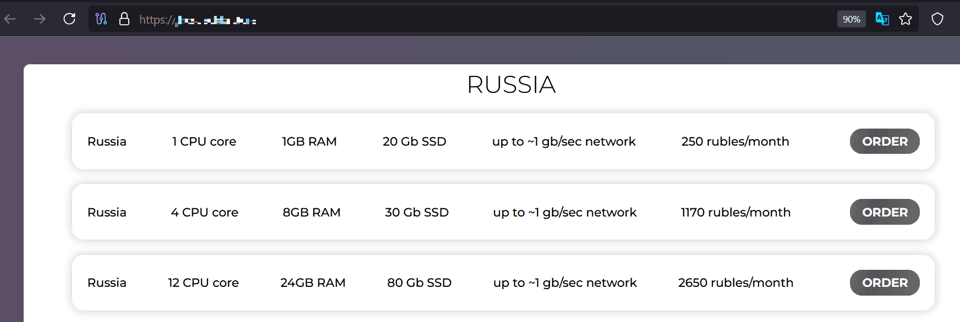
Figure 5. Webpage of one of the newest server services offered on XSS (automatically translated from the original in Russian).
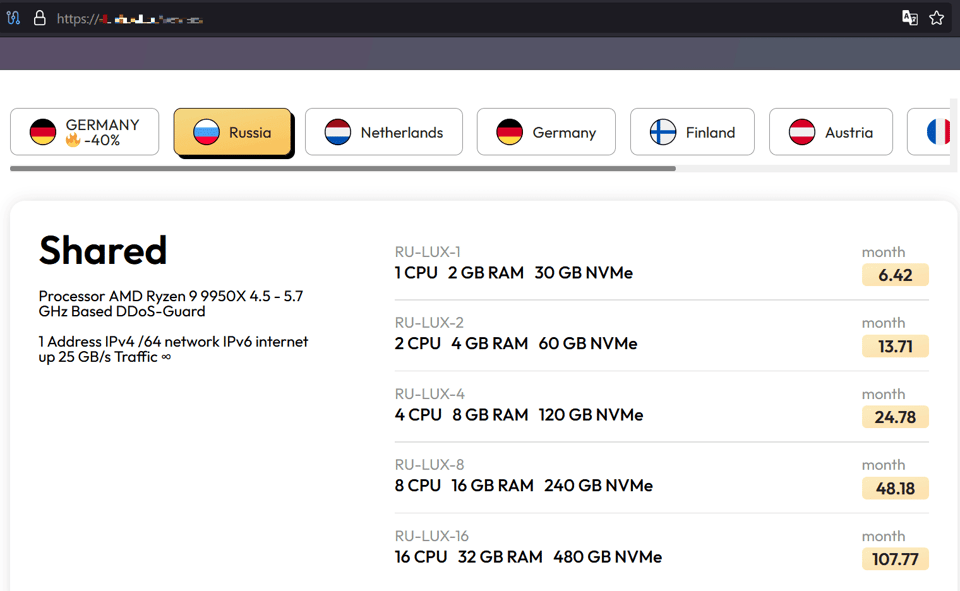
Figure 6. Webpage of one of the pinned server services offered on XSS.
For the three services compared here, we selected Russian servers with the most basic configuration settings.
Considering the prices for the most basic offer from the three providers, we calculate an average cost of US$3.63 per month.
Delivery mechanisms
As for delivery mechanisms, let’s consider the cost of acquiring a phishing kit:
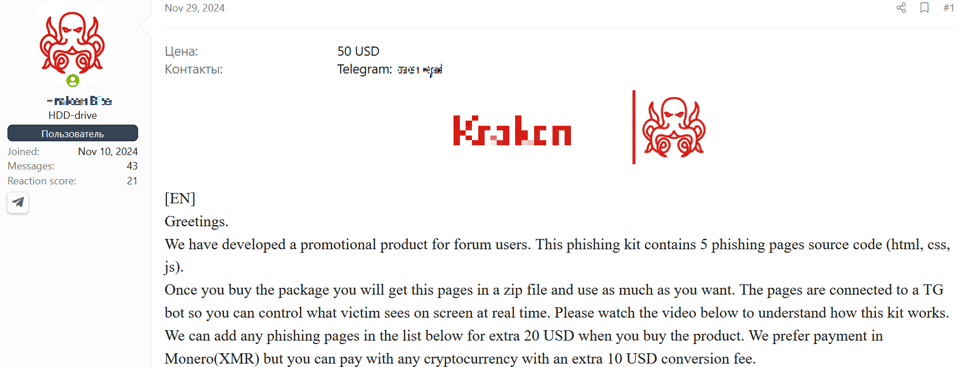
Figure 7. A reputable adversary offers an all-in-one phishing kit on the XSS forum.
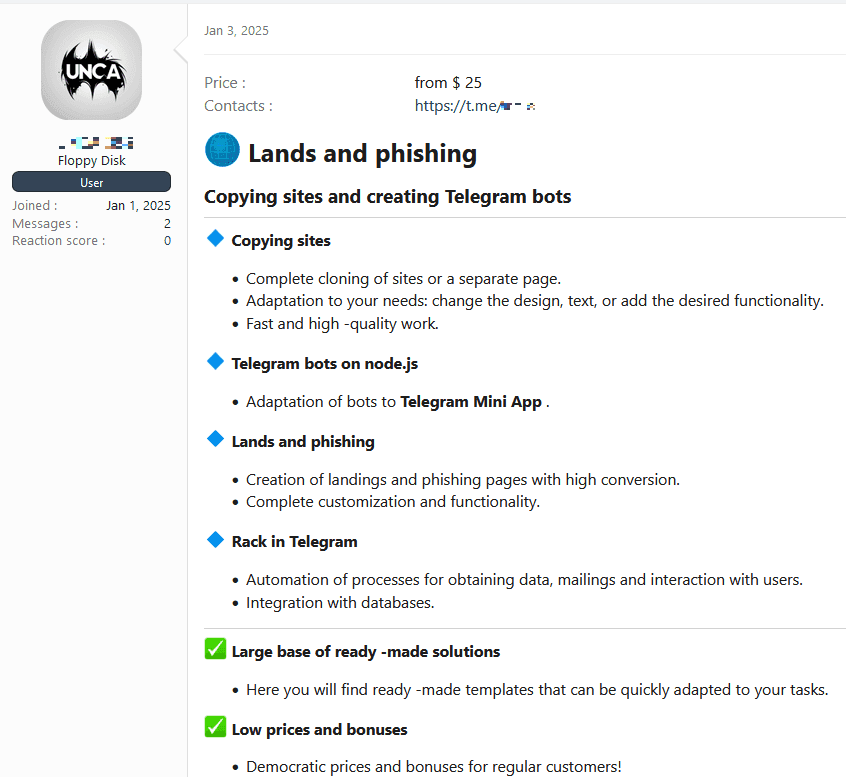
Figure 8. A new user offers an all-in-one phishing kit on the XSS forum.
Comparing the two phishing kits mentioned above, we can estimate an average price of US$37.5 for this type of service.
Evasion services
In credential theft campaigns, buying or renting a crypter is crucial for ensuring that the infostealer remains undetected by security solutions. Without effective obfuscation, stealers are quickly flagged, which drastically reduces their lifespan and consequent effectiveness. Therefore, using cybercriminal underground language, a crypter's primary aim is to make the stealer FUD (Fully Undetectable) by obfuscating its code and bypassing security detections, helping extend the operational lifespan of a stealer.
We decided to analyze the XSS forum in the search for crypters. Our selection criteria were pinned threads and the ones with the greatest number of replies. The screenshots below are two examples of crypters that fit into our selection criteria:
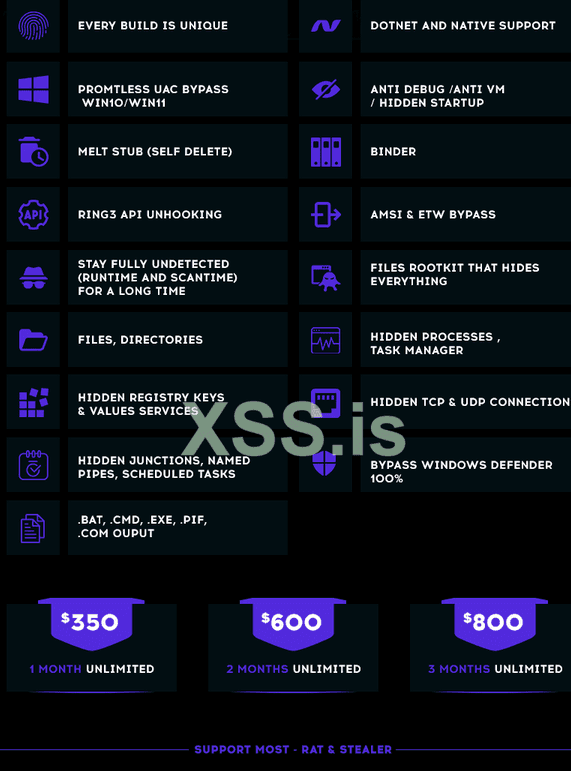
Figure 9. Advertisement of a malware crypter in XSS, first announced in late 2023 but last updated in February 2025.
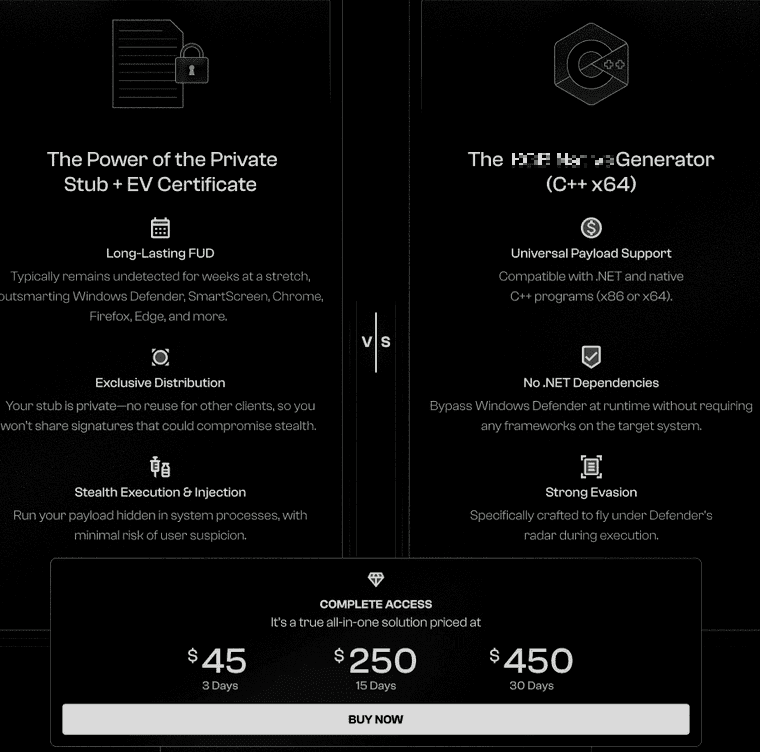
Figure 10. Advertisement of a malware crypter in XSS, first announced in January 2025.
It is possible to check that crypter prices are quite homogenous, costing an average of US$400 per month.
YouTube SEO costs
In recent years, cybercriminals and threat actors (TAs) have increasingly leveraged social media platforms to propagate malicious software. Among these platforms, YouTube has become a particularly effective tool due to its wide reach, global audience, and user trust in its content.
Threat actors exploit the trustworthiness and accessibility of YouTube to attract unsuspecting users into downloading malware. Some of the most common tactics include:
- Malicious Links in Video Descriptions: Threat actors upload videos claiming to provide cracked software, game cheats, hacking tools, or legitimate software installers. The video description commonly contains a link, usually shortened (e.g., using Bitly or TinyURL), that leads to a malicious download.
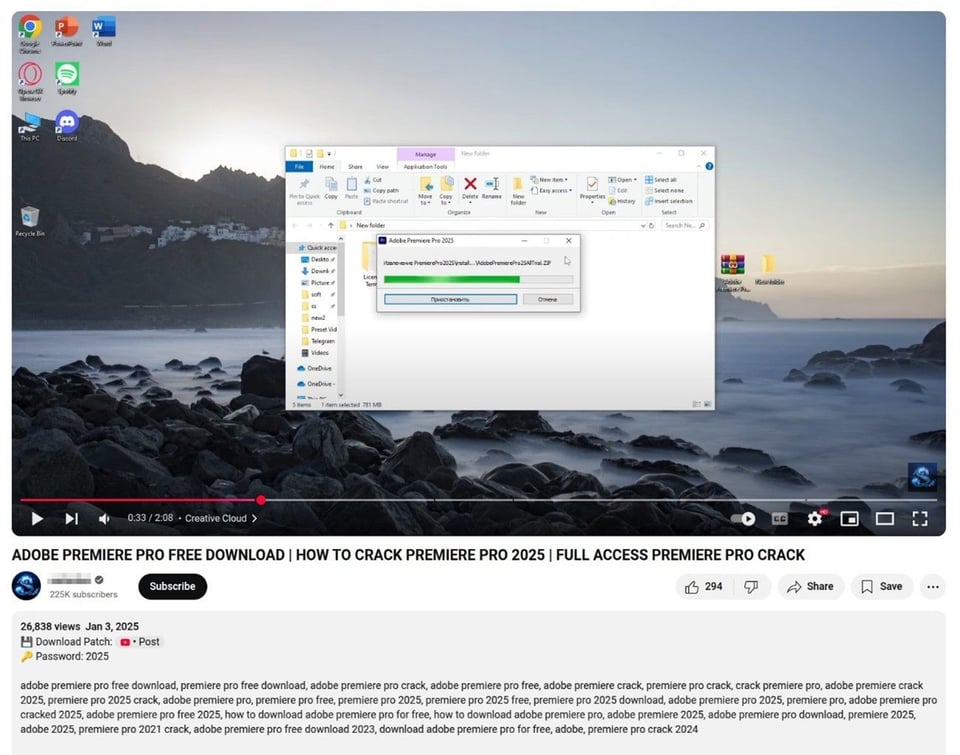
Figure 11. An example of a YouTube video whose aim is to distribute malware through an instructional video.
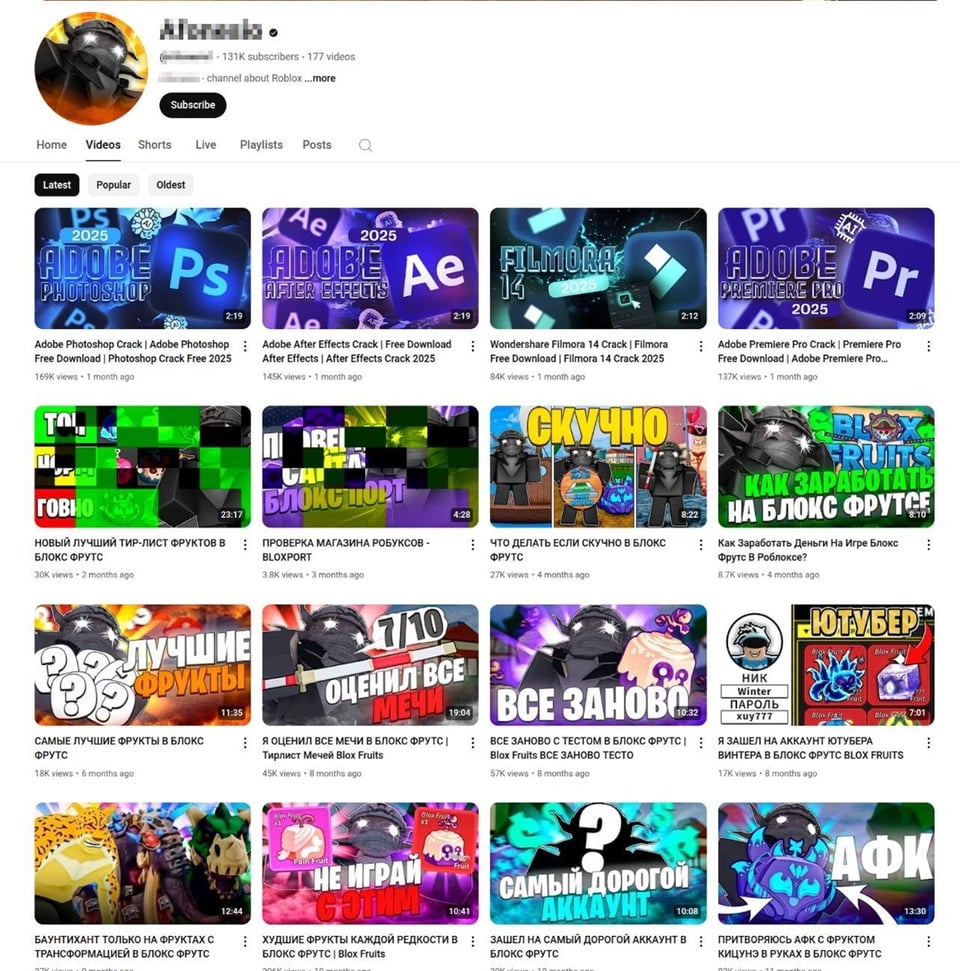
Figure 12. The video below is one of 4 posted in a previously Roblox-themed popular channel.
- SEO and Algorithm Manipulation: Threat actors optimize video titles, descriptions, and tags to align with trending search terms, increasing the visibility of their malicious content. Videos often mimic popular tutorials, such as software installation guides or technology reviews. There are numerous services promoted on underground forums specifically designed to enhance the SEO of videos used to spread malware. The cost of these services is around US$50 per week.

Figure 13. Advertisment of SEO service on an underground forum.
We spotted the following SEO manipulation service advertisement in an underground forum and decided to privately contact the seller to learn their prices, which are detailed below:
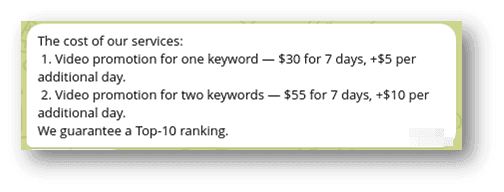
Figure 14. The price scheme refers to the service advertised on the forum - check figure 13.
- Use of Compromised or Fake Accounts: To establish credibility, TAs may use compromised or newly created accounts that appear legitimate, often with profile pictures, uploaded content, and fake positive comments to boost credibility. In the following image, we can see an advertisement offering a YouTube account with 174k subscribers for only US$350:
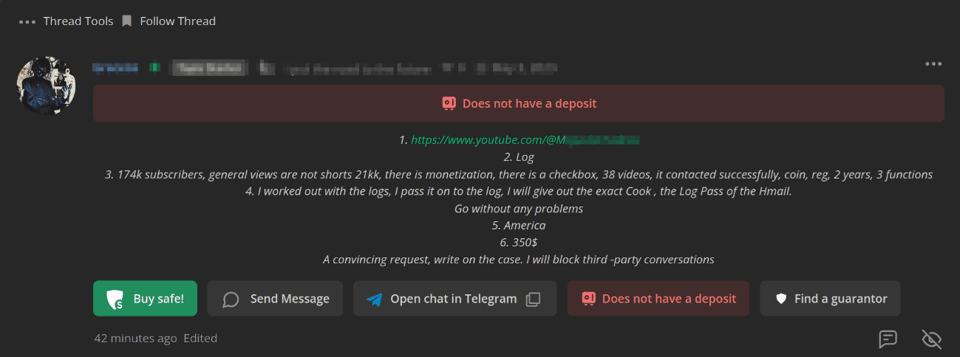
Figure 15. Sale of a compromised YouTube account advertised on an underground forum.
What is then the estimated cost of running a YouTube malware distribution campaign?
- YouTube Account: US$350
- Video Production (2 videos): US$100
- SEO Services: US$200
- Engagement Boost (2 videos): US$60
Running a YouTube-based malware campaign is relatively low-cost compared to the potential financial gain, especially if the malware is designed to steal credentials, cryptocurrency wallets, or sensitive corporate data. With an initial investment of roughly US$500 - US$1000, a threat actor can launch a fairly professional-looking campaign, especially targeting users looking for free software or cracks. This low barrier to entry makes YouTube a highly attractive platform for cybercriminals.
Group structure and salaries
The emergence of traffers teams marks a transformation in the credential theft ecosystem, introducing a new professionalized approach to credential theft campaigns – and impacting on its efficiency and cost. Traffers teams are groups specialized in credential theft operations, operating within a structured, pyramid-like hierarchy. Administrators invest in malware, obfuscation tools, and distribution infrastructure, while operators focus on disseminating malware and collecting stolen data.
Upon a brief analysis of the latest traffer team recruitment announcements on Zelenka, we could identify that payment varies between 70% and 80% of the monetization of collected logs:
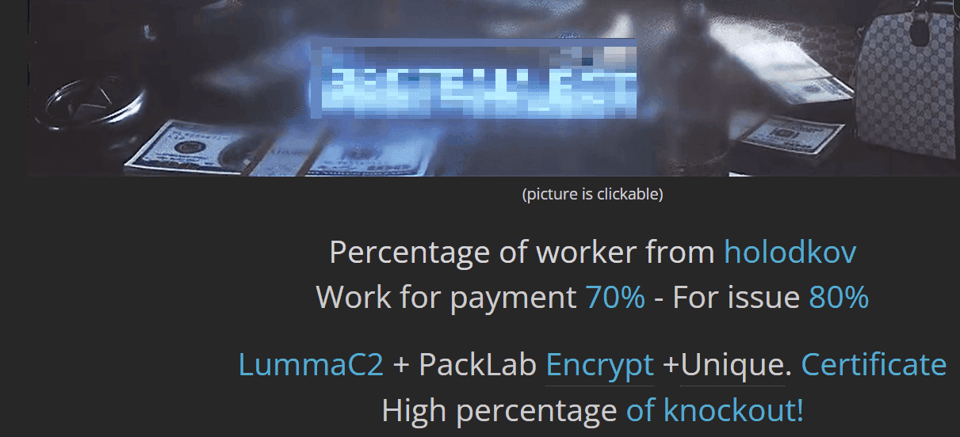
Figure 16. A traffer team recruitment post on Zelenka (automatically translated from the original in Russian).
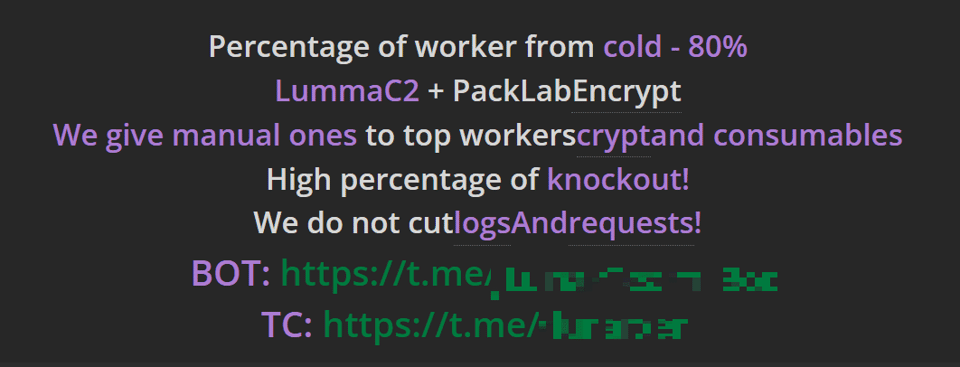
Figure 17. A traffer team recruitment post with higher payment rate on Zelenka (automatically translated from the original in Russian).
Reviewing the comments section of the recruitment posts, we can have a glimpse of how much the operators make with a traffer campaign. The following screenshots refer to the operation illustrated in figure 16:
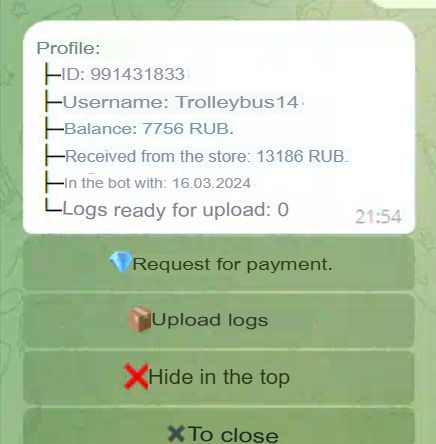
Figure 18. The traffer operator "Trolleybus14", who joined the team on March 16, 2024, had earned 13,186 rubles (around US$141 at the time) by April 14, 2024 (automatically translated from the original in Russian).
In almost a month, Trolleybus14 earned an average of 454 rubles per day of activity (around US$5 at that time).
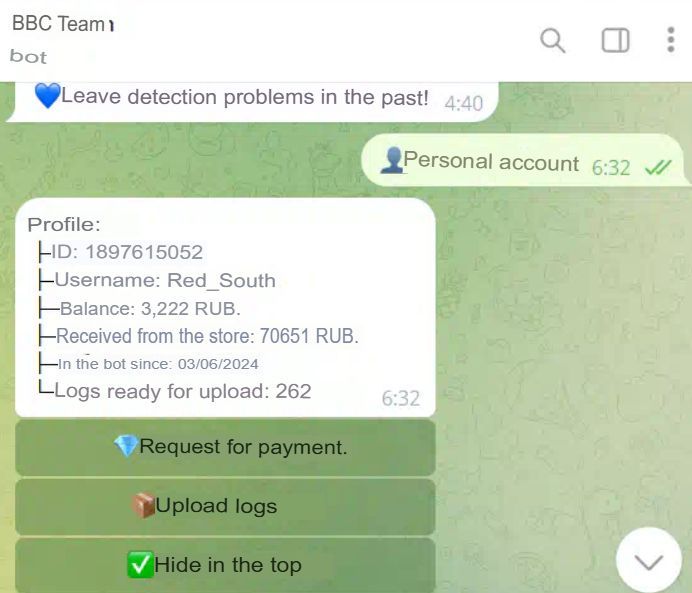
Figure 19. The traffer operator "Red_South", who joined the team on March 06, 2024, had earned 70,651 rubles (around US$759 at that time) by April 21, 2024 (automatically translated from the original in Russian).
In a month and a half of activity, Red_Soutg earned an average of 1,535 rubles per day of activity (around US$16 at that time).
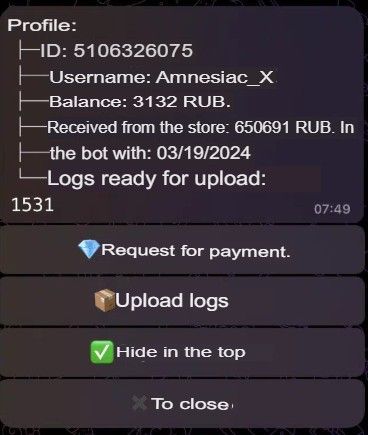
Figure 20. The traffer operator "Amnesiac_X", who joined the team on March 19, 2024, had earned 650,691 rubles (around US$7,053 at that time) by April 05, 2024 (automatically translated from the original in Russian).
Unlike the other two examples above, who were earning an average of 994 rubles per day (approximately US$10.7 at that time), Amnesiac_X made an average of 38,275 rubles per day of activity (around US$414 at that time) in less than three weeks. This significant disparity suggests that traffer operators' earnings can vary widely, probably due to the level of personal and financial investment the worker puts on. Likely, the higher paid criminal employed some of the tools that we have mentioned throughout this study – SEO services, buying compromised YouTube accounts, etc. The ones who did not invest as much in their operation likely are the ones earning less money, so it is hard estimating average earnings per traffer worker. Therefore, it is also challenging to accurately estimate the personnel costs incurred by traffer administrators. Aditionally, the number of affiliates can vary greatly – while some groups have 200 traffer operators, others can mount up to 1,000 or more, with discrepant earnings.
Conclusion: final budget
This study calculates the average price for the following aspects of a malware-based credential theft campaign: the average infostealer rental fee is US$250, with basic subscriptions at US$3.63 per month and crypters averaging US$400. Other costs include US$350 for a YouTube account, US$100 for two videos, US$200 for SEO, and US$60 for engagement boosts. Based on these calculations, the minimum cost to launch a credential theft campaign is US$1,363. This figure represents the bare minimum investment required to set up such operations. This may seem like a high upfront cost, but our next publication will explore how much a cybercriminal can make in earnings with such a campaign. Does it pay off? Stay tuned for the answer!
BLOG